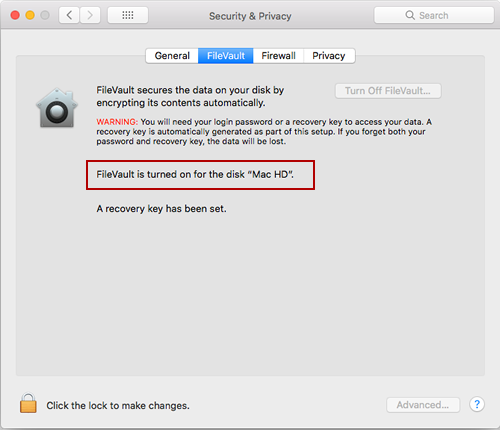
Cracking Encryption: Despite Benefits, Technology Still Not Widely Used to Combat Multi-Million Dollar Breaches

Unencrypted data being transmitted over HTTP increases the risk of hacking says Kaspersky Labs- Technology News, Firstpost

Today Tip: - Don't share your data on unencrypted “HTTP” websites/apps. Below picture show all details entered: Device, gender, location, screen resolution. Now imagine purchasing or registering your Bank info in unsecured