User authentication-authorization concept icon. Software development kit idea thin line illustration. Data encryption. Privacy protection. Application Stock Vector Image & Art - Alamy

The Hidden Costs of DIY Cloud Data Lakes #2: Identity Management and Authentication (Single Sign-On) - Cazena | Cazena
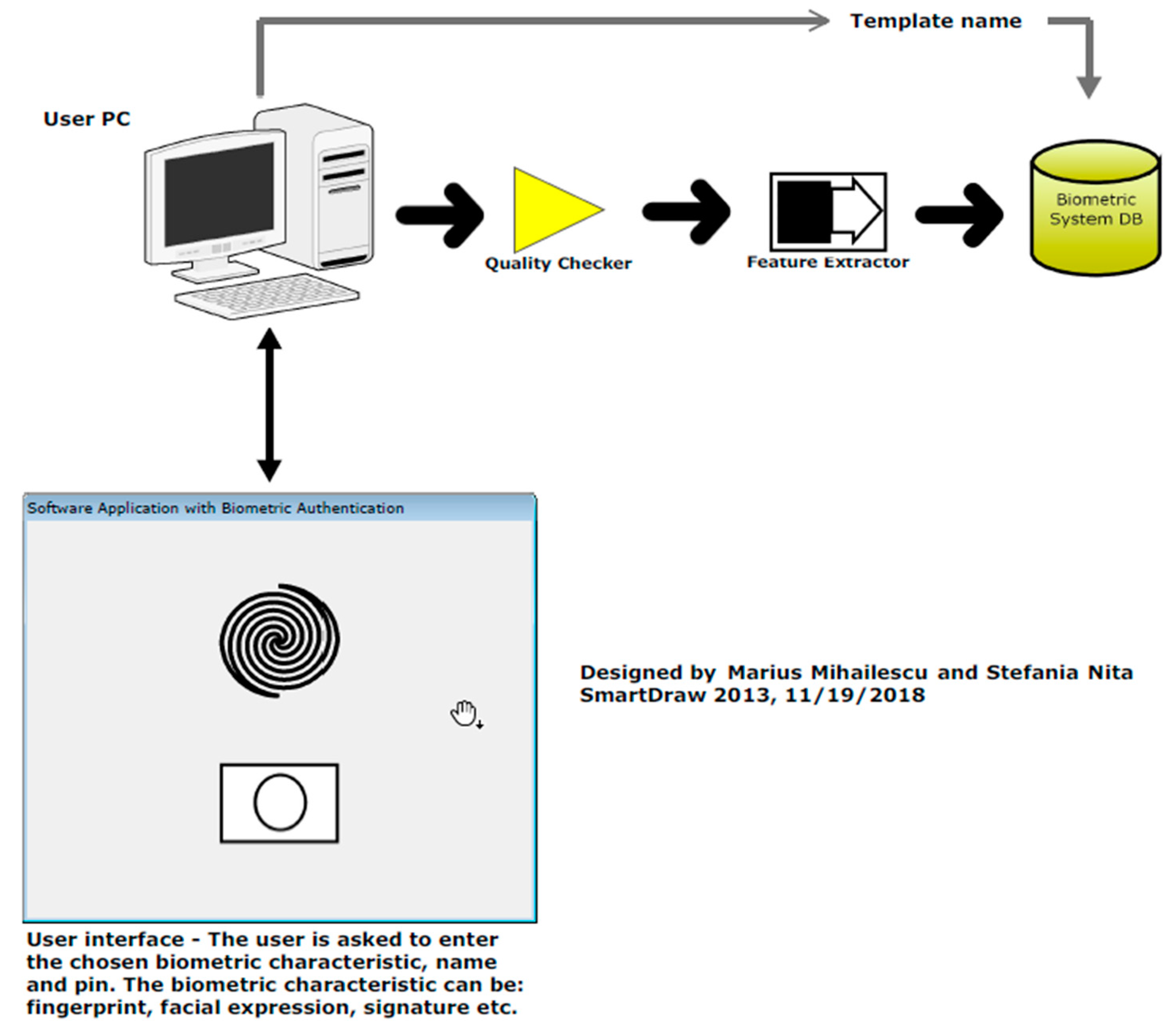
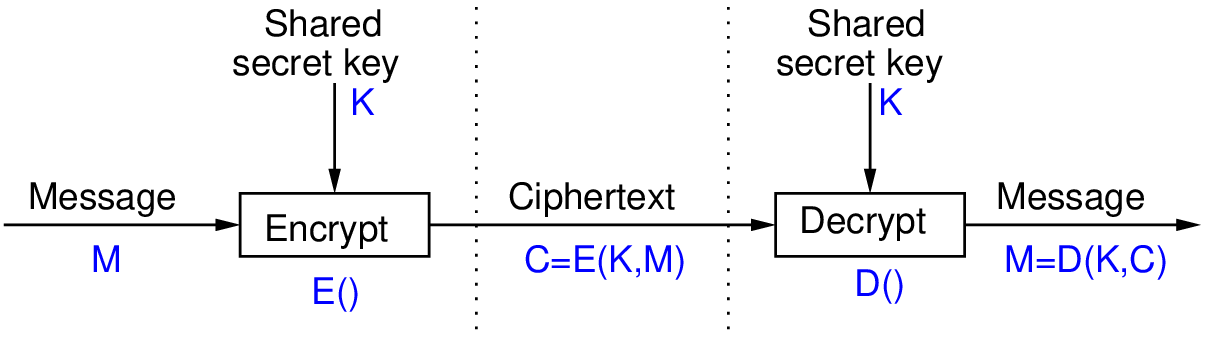
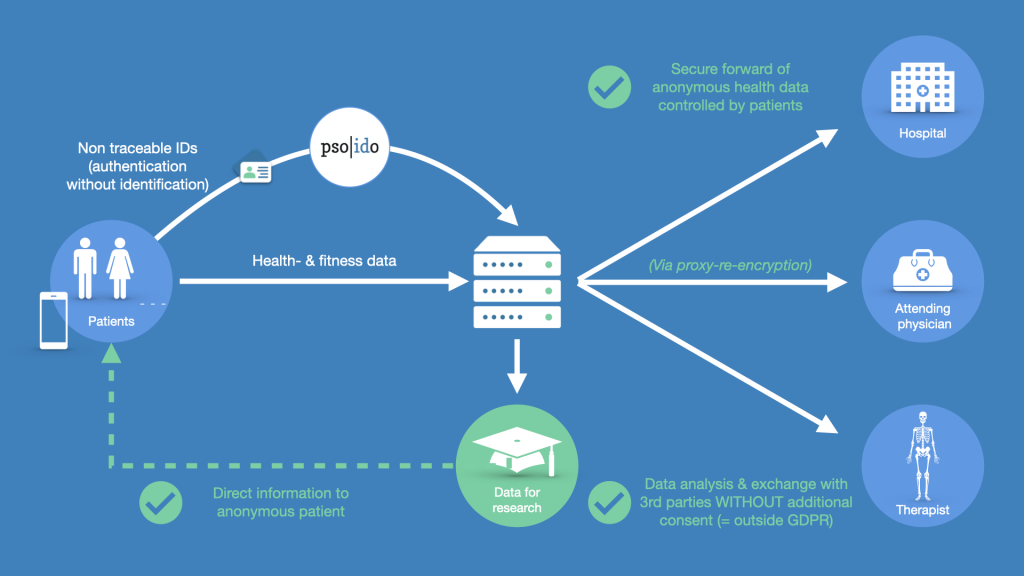
Cryptography | Free Full-Text | Security and Cryptographic Challenges for Authentication Based on Biometrics Data

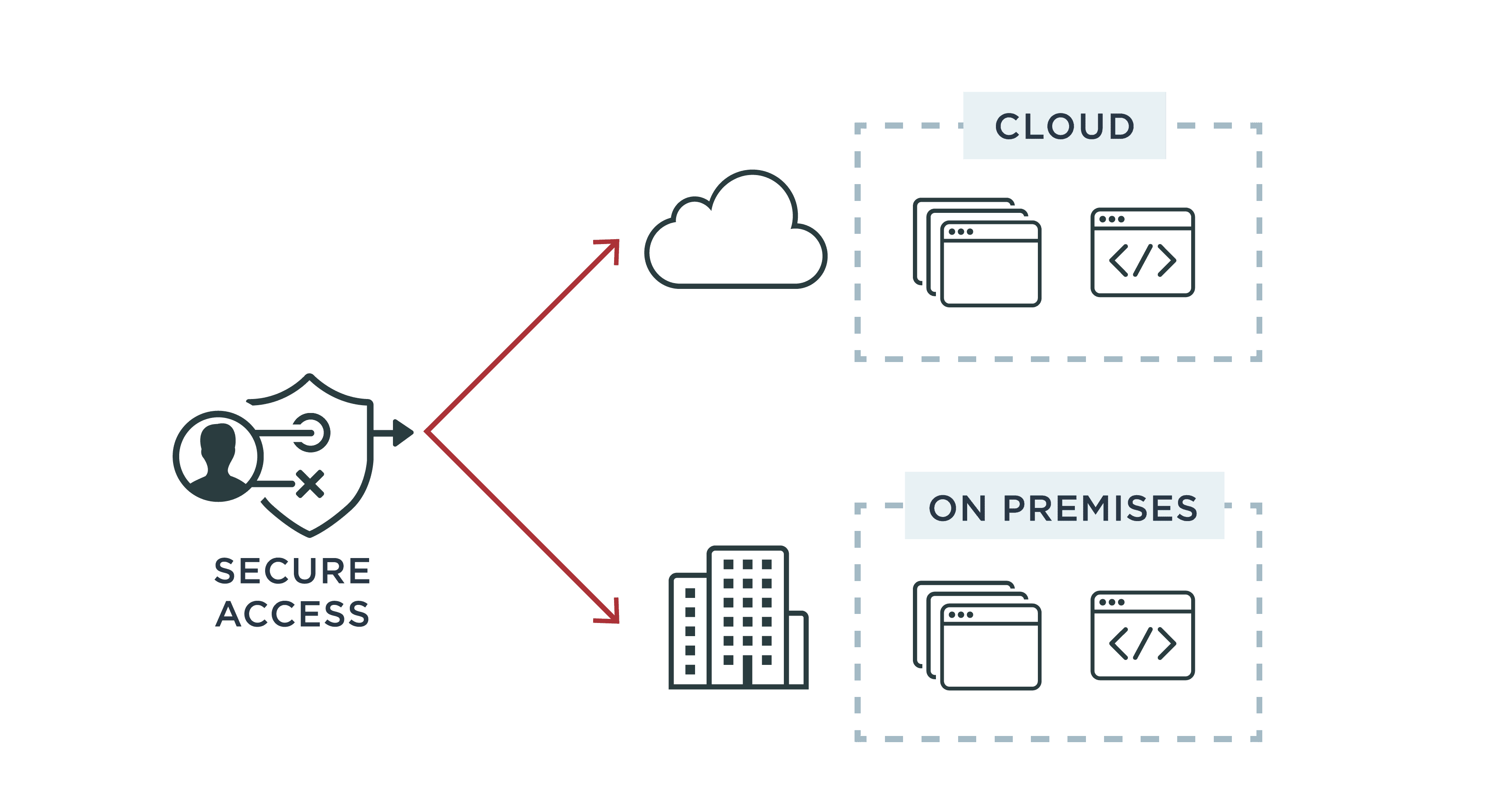
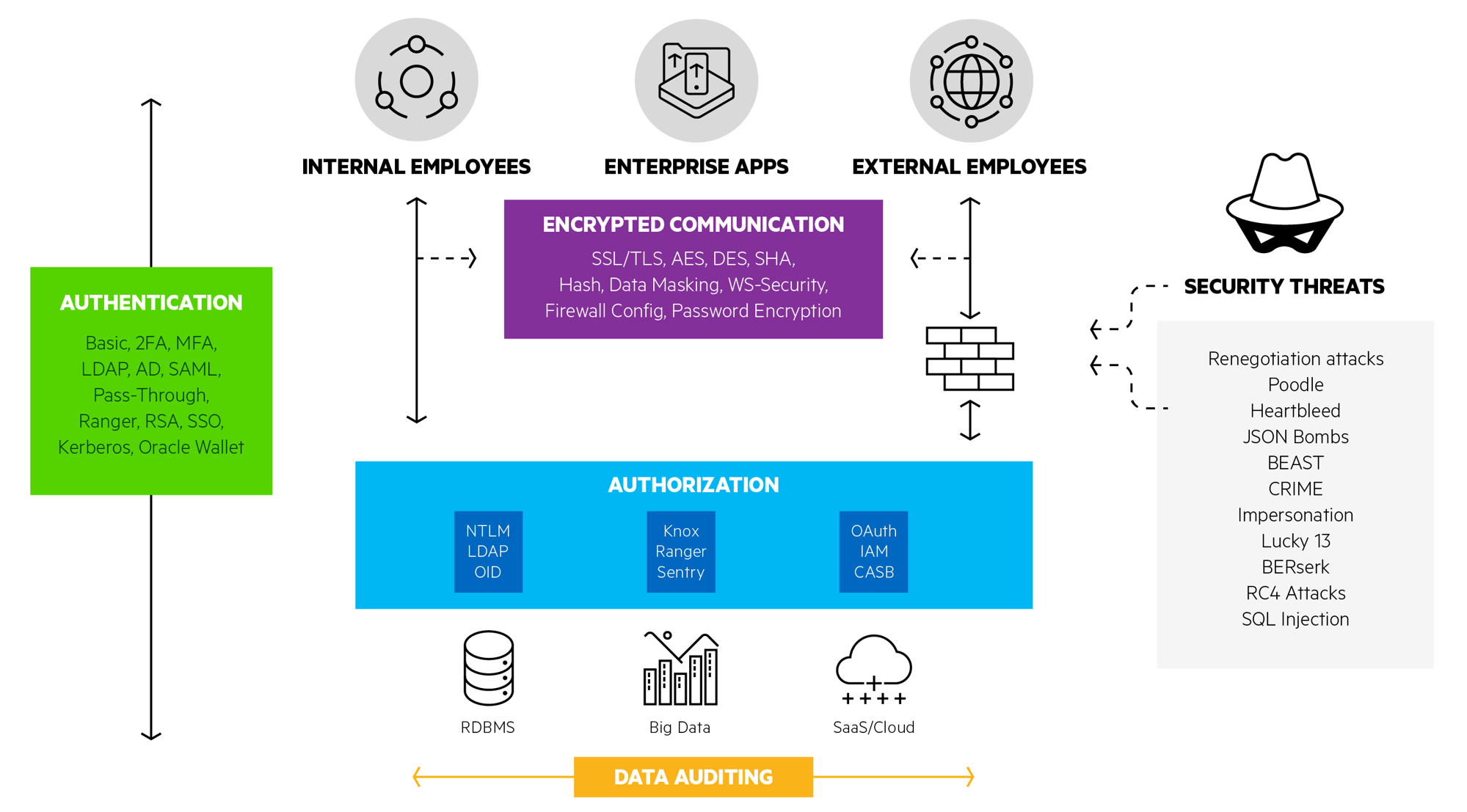
Subsurface Data Management: Overview of authentication and authorization on AWS implementation of OSDU™ Data Platform | AWS for Industries

PCI Requirement 3.2 - Do Not Store Sensitive Authentication Data After Authorization | PCI Demystified



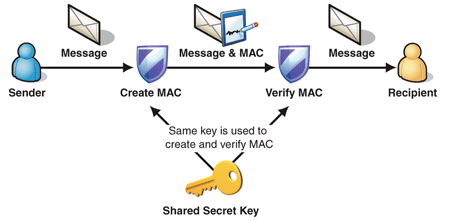
![MS-AUTHSOD]: Data Origin Authentication (Signing) | Microsoft Learn MS-AUTHSOD]: Data Origin Authentication (Signing) | Microsoft Learn](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-authsod/ms-authsod_files/image027.png)