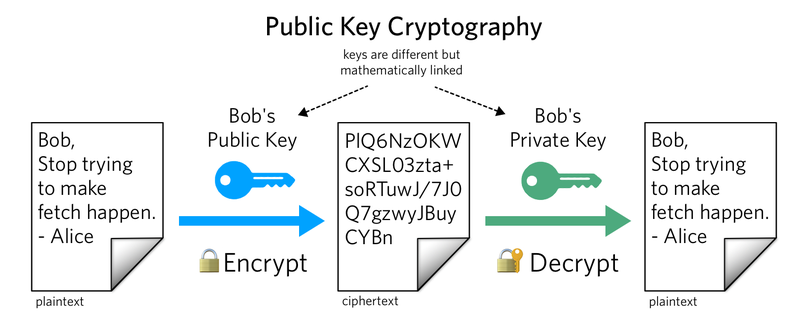
Hybrid Symmetric Cryptography: A System for Symmetric Key Cryptography using Dynamic Key & Linear Congruential Generator: Mehmood, Zeenat, Khan, Mohd Ilyas, Siddiqui, Abdul Moiz: 9783659483042: Amazon.com: Books

RNG — The Secret of Cryptography. Random Generator Number is the core… | by Dinh-Cuong DUONG | Problem Solving Blog | Medium

Pseudo-random permutation generators and cryptographic composition | Proceedings of the eighteenth annual ACM symposium on Theory of computing
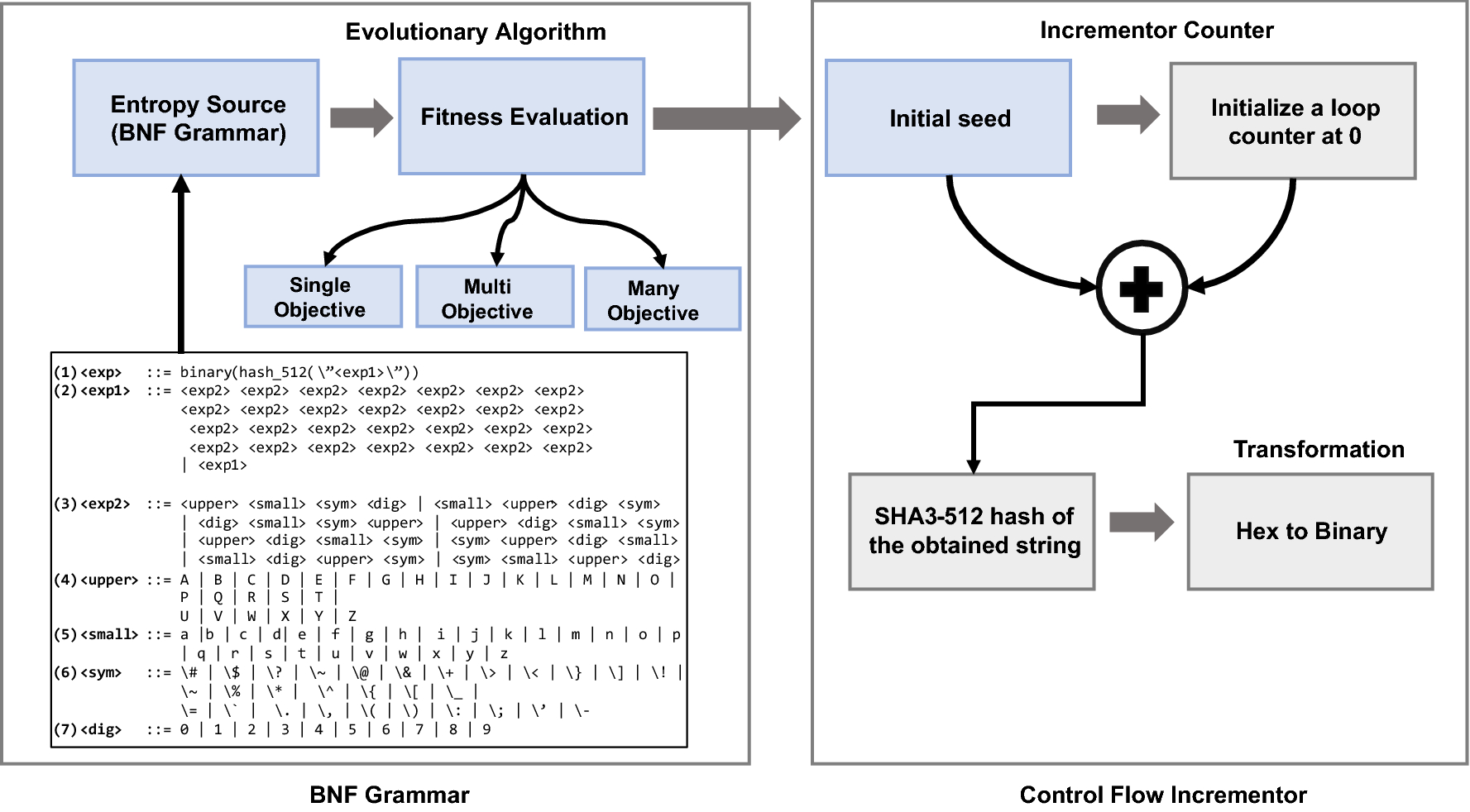
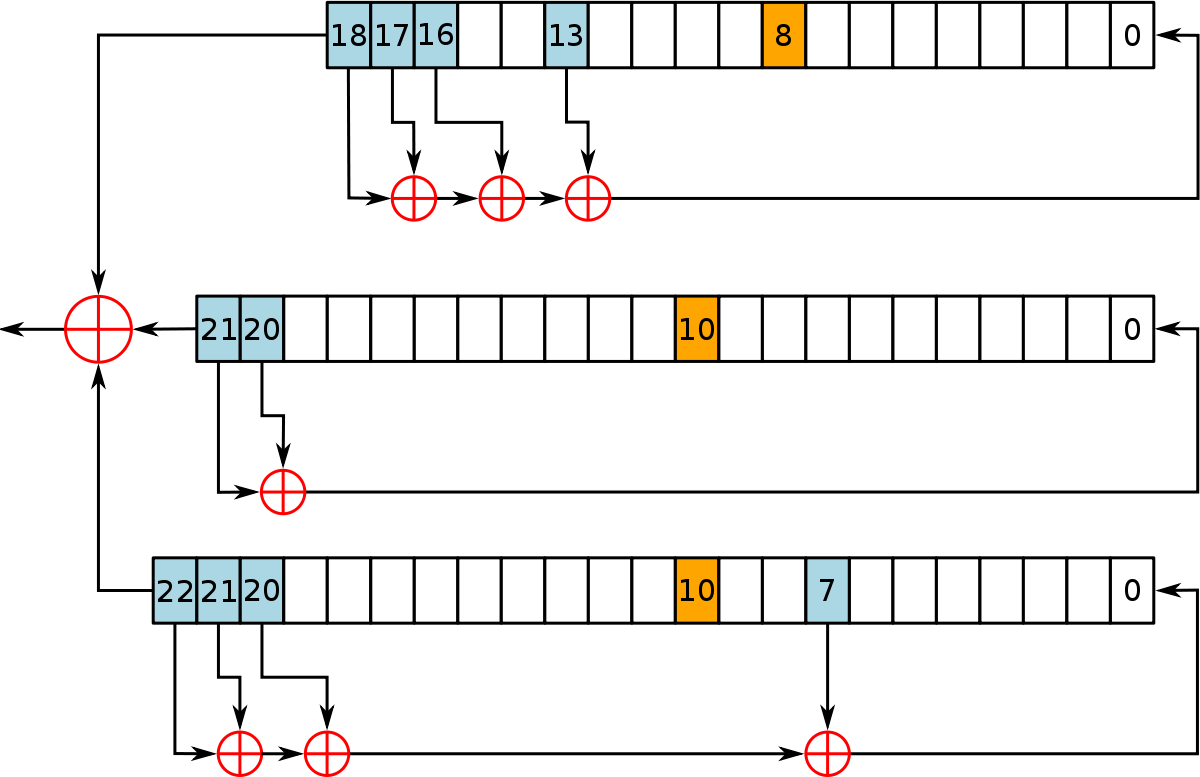
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports

Distributing a Private Key Generator in Ad hoc Networks: Authority Distribution Using Threshold Cryptography: Stenberg, Eystein Måløy: 9783838387710: Amazon.com: Books

why XOR is recommended/Used in every paper I read for encryption and decryption stream cipher? - Cryptography Stack Exchange
![PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/52d197f4c8881618c40bd36ef98d7cef2c5148f0/2-Figure2-1.png)
PDF] Three-Pass Protocol Implementation in Vigenere Cipher Classic Cryptography Algorithm with Keystream Generator Modification | Semantic Scholar
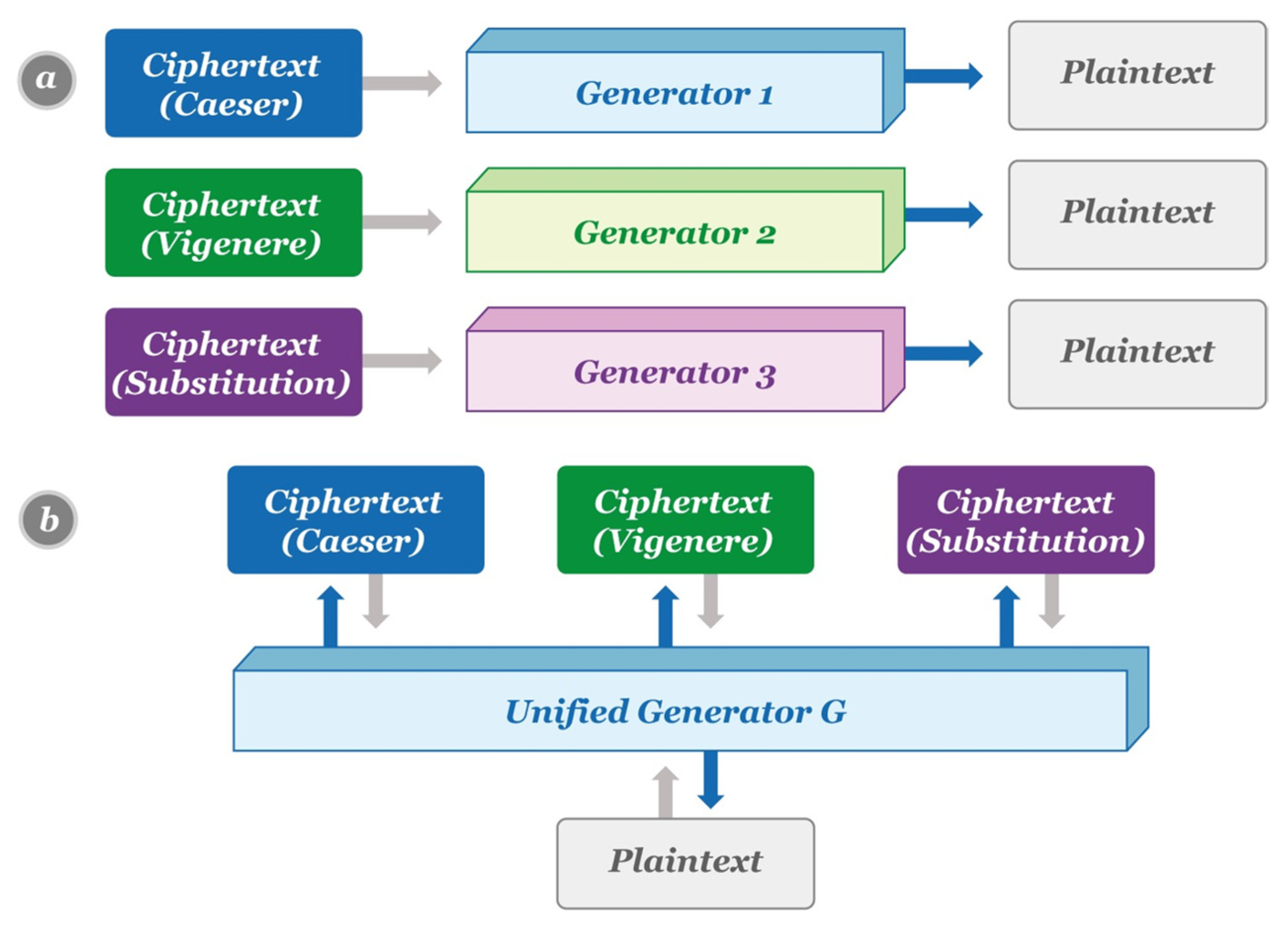
Automated cryptocode generator is helping secure the web | MIT News | Massachusetts Institute of Technology



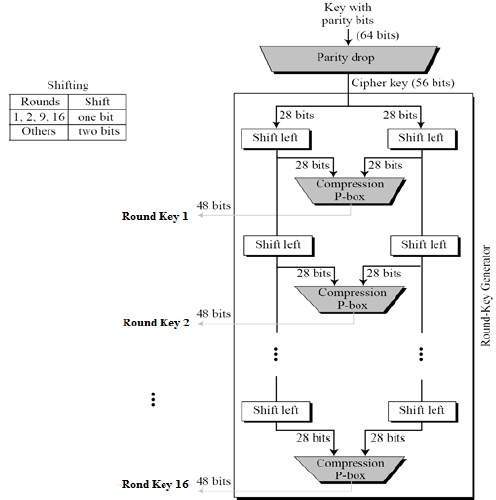
![PDF] Hardware Random number Generator for cryptography | Semantic Scholar PDF] Hardware Random number Generator for cryptography | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/d40db1ffcac69cd2bab55d7f50159922eaa2b5bf/2-Figure1-1.png)