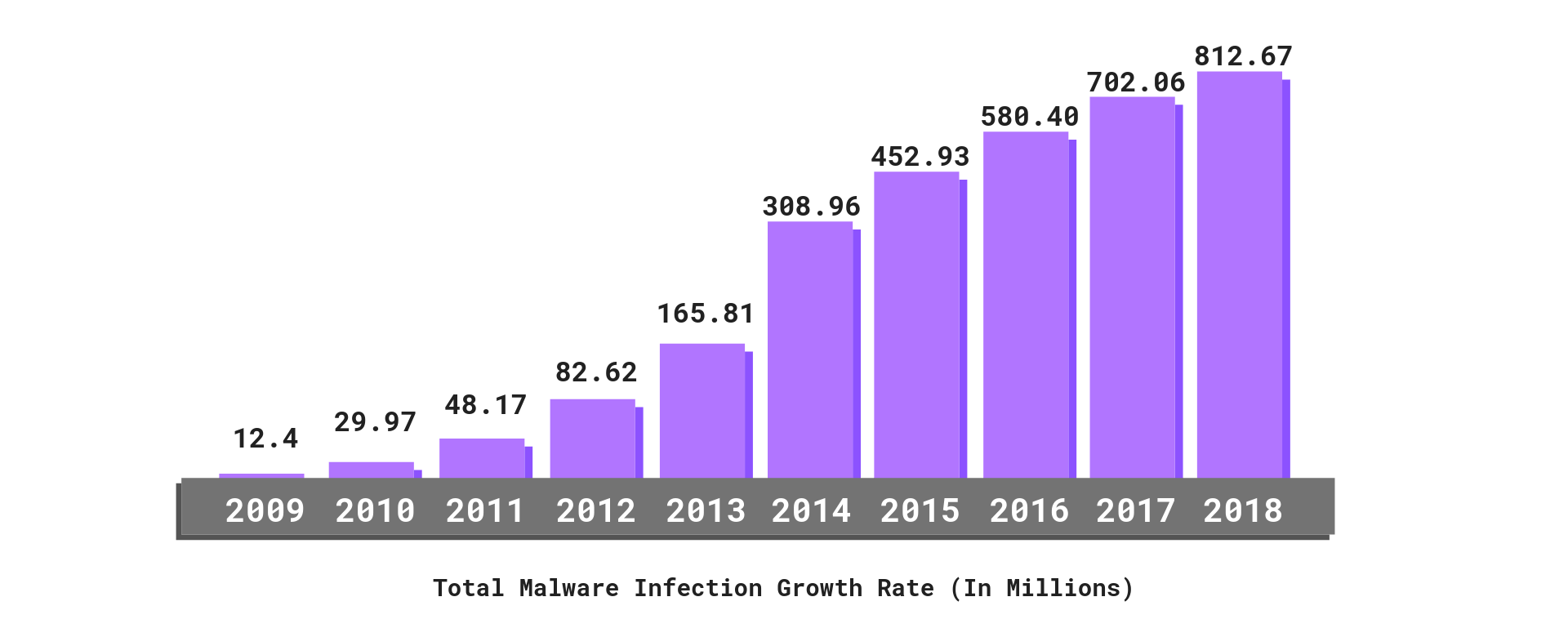
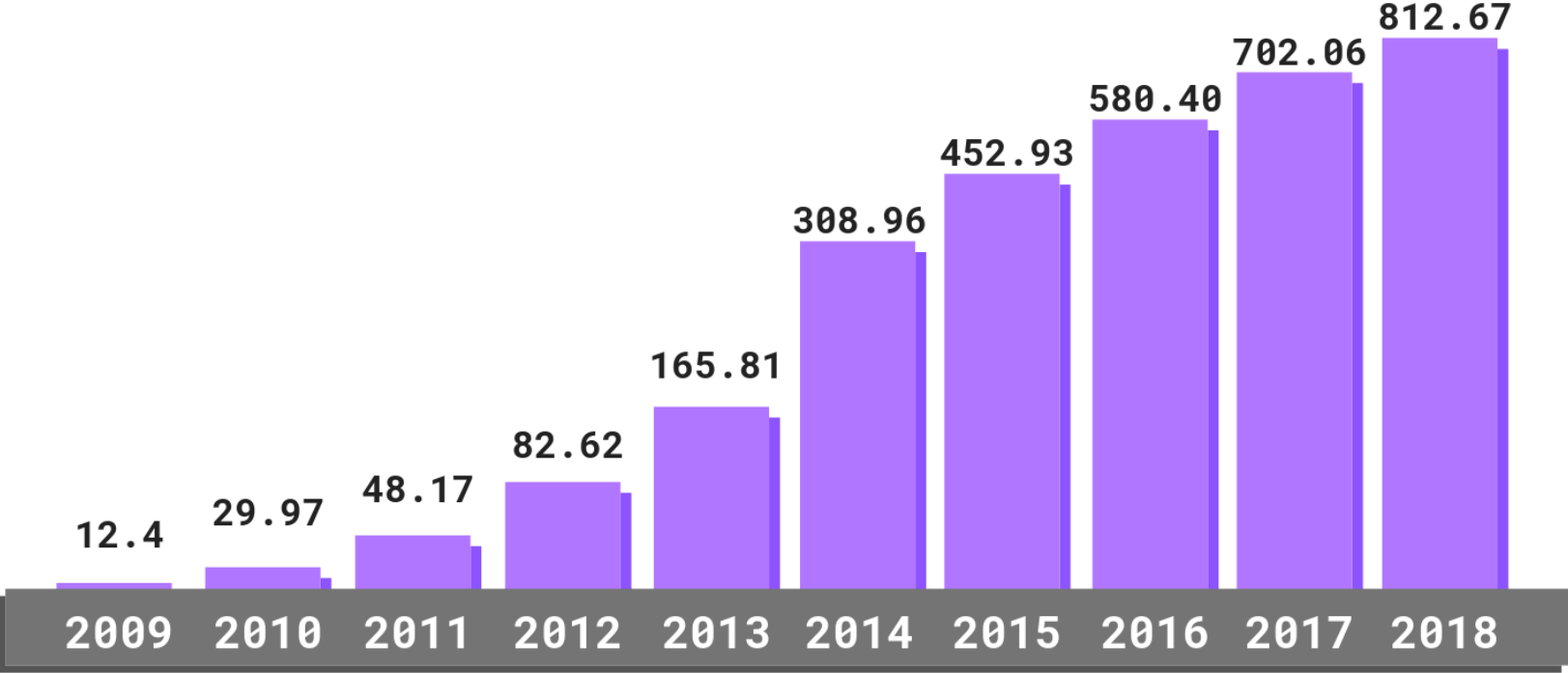
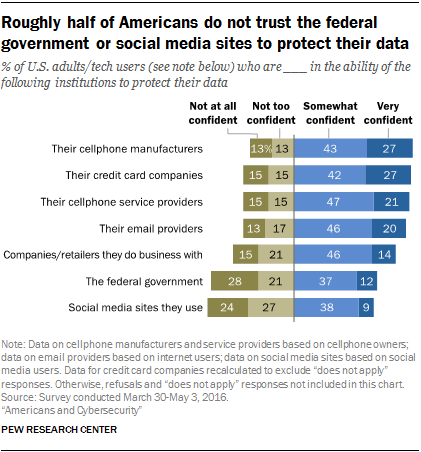
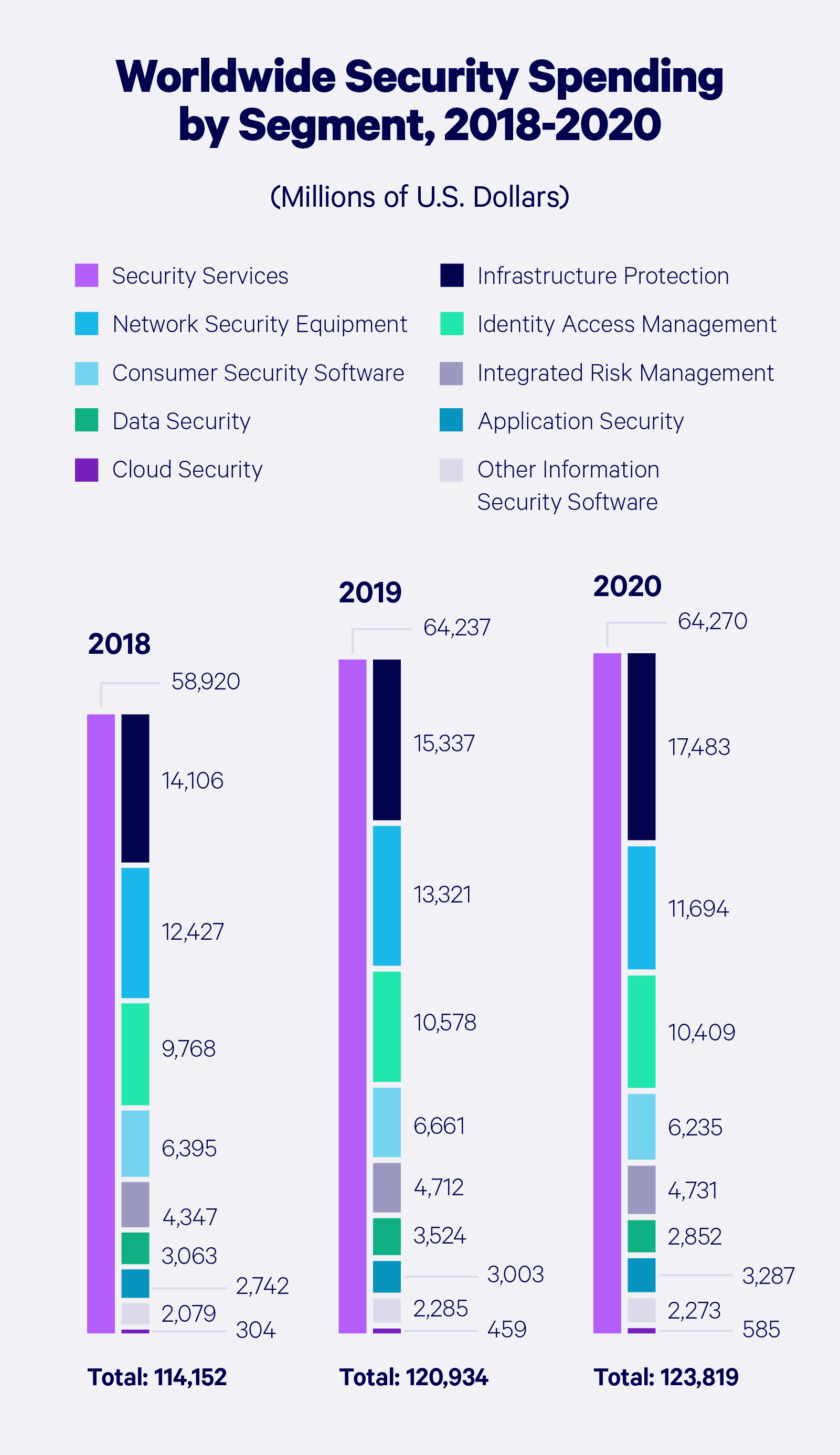
Operational Technology (OT) & Industrial Cybersecurity: 10 Things You Need To Know | Engineering USA

Cyber Security: Technologies and Global Markets Report 2022: Data from 2020, Estimates for 2022 & Projections to 2024

Are You Spending Too Much (or Too Little) on Cybersecurity? | Data Center Knowledge | News and analysis for the data center industry




![10 Cybersecurity Statistics in 2019 [Infographic] - TitanFile 10 Cybersecurity Statistics in 2019 [Infographic] - TitanFile](https://www.titanfile.com/wp-content/uploads/2019/05/Cybersecurity-Statistics-2019-Infographic-2.png)